Podman
This method is supported by R2DevOps community.
This page describes how to set up a self-managed instance of R2Devops using podman.
💻 Requirements
- GitLab instance version >=17.7
- The system requires a Linux server. It runs in 🕸 podman containers using a
yaml configuration. Specifications:
- OS: Ubuntu or Debian
- Hardware
- CPU x86_64/amd64 with at least 2 cores
- 4 GB RAM
- 250 GB of storage for R2Devops
- Network
- Users must be able to reach the R2Devops server on TCP ports 80 and 443
- The R2Devops server must be able to access internet
- The R2Devops server must be able to communicate with GitLab instance
- The installation process requires write access to the DNS Zone to set up R2Devops domain
- If the server is not reachable from internet or if you want to use your own certificate for HTTPS, you need to be able to generate certificate during the installation process for R2Devops domain
- Installed software
unqualified-search-registries = ["docker.io"]
🛠️ Installation
📥 Setup your environment
- Clone the repository on your server
git clone https://github.com/r2devops/self-managed.git r2devops
cd r2devops - Create your configuration file
cp .env.example .env
📋 Organization
In your .env file:
-
If you want to connect R2Devops to a specific GitLab group only: add the path of the group in
ORGANIZATIONvariable (to run the onboarding, you must be at least Maintainer in this group).envORGANIZATION="<group-path>" -
If you want to connect R2Devops to the whole GitLab instance: let the
ORGANIZATIONvariable empty (to run the onboarding, you must be a GitLab instance Admin).envORGANIZATION=""
📄 Domain name
-
Edit the
.envfile by updating value ofDOMAIN_NAMEandJOBS_GITLAB_URLvariables.envDOMAIN_NAME="<r2devops_domain_name>"
JOBS_GITLAB_URL="https://<url_of_your_gitlab_instance>"Example with domain name 'r2devops.mydomain.com' for R2Devops and 'gitlab.mydomain.com' for GitLabDOMAIN_NAME="r2devops.mydomain.com"
JOBS_GITLAB_URL="https://gitlab.mydomain.com" -
Create DNS record
- Name:
<r2devops_domain_name> - Type:
A - Content:
<your-server-public-ip>
- Name:
A certificate will be auto-generated using Let's encrypt at the application launch
🦊 GitLab OIDC
R2Devops uses GitLab as an OAuth2 provider to authenticate users. Let's see how to connect it to your GitLab instance.
Create an application
Choose a group on your GitLab instance to create an application. It can be any
group. Open the chosen group in GitLab interface and navigate through
Settings > Applications:
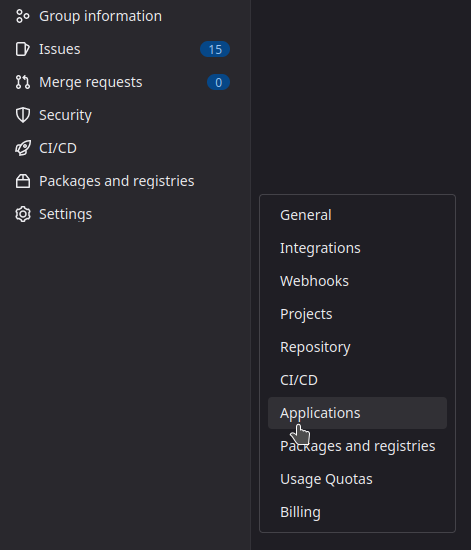
Then, create an application with the following information :
- Name:
R2Devops self-managed - Redirect URI :
https://<r2devops_domain_name>/api/auth/gitlab/callback - Confidential:
true(let the box checked) - Scopes:
api
Click on Save Application and you should see the following screen:
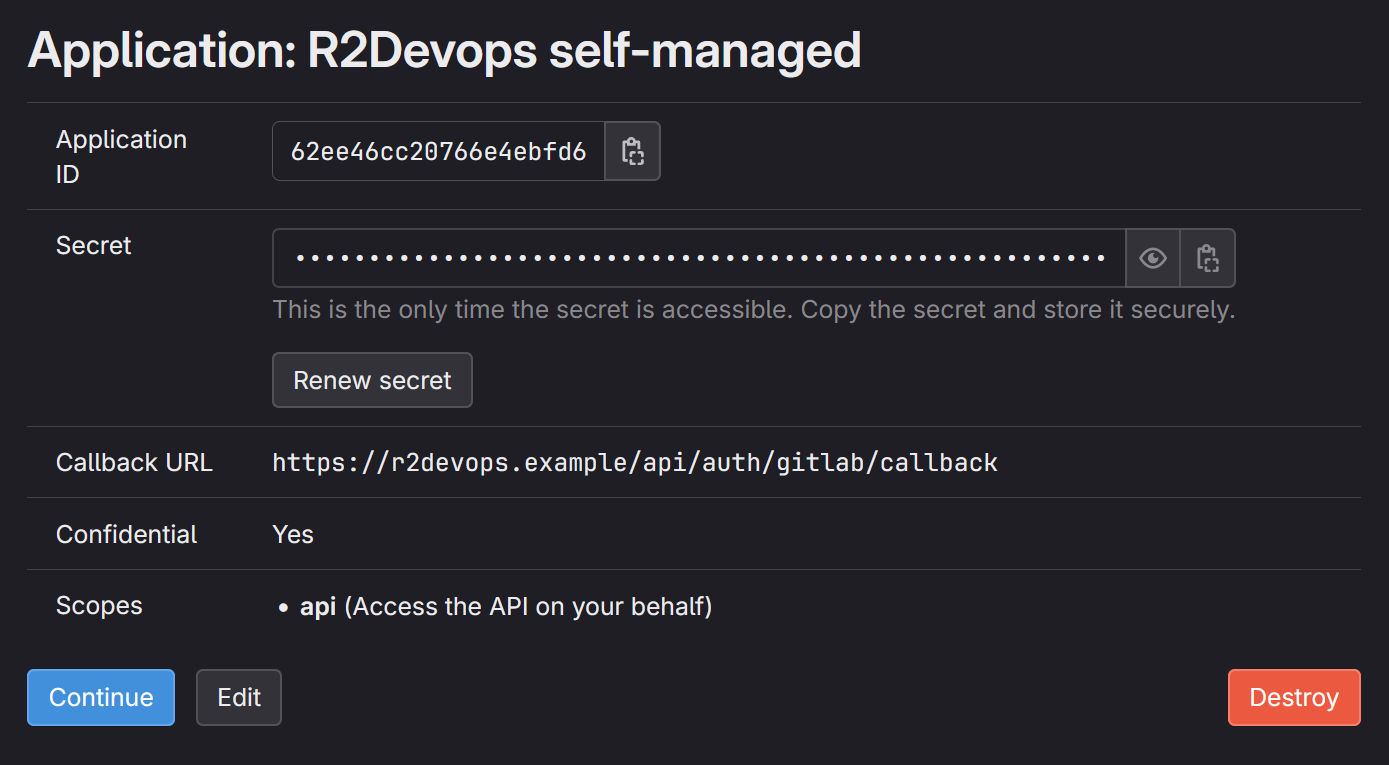
Update the configuration
In .env file:
- Copy/paste the
Application IDand theSecretfrom the application you just created.envGITLAB_OAUTH2_CLIENT_ID="<application-id>"
GITLAB_OAUTH2_CLIENT_SECRET="<application-secret>"
🔐 Generate secrets
Generate random secrets for all components:
sed -i "s/REPLACE_ME_BY_SECRET_KEY/$(openssl rand -hex 32)/g" .env
sed -i "s/REPLACE_ME_BY_JOBS_DB_PASSWORD/$(openssl rand -hex 16)/g" .env
sed -i "s/REPLACE_ME_BY_JOBS_REDIS_PASSWORD/$(openssl rand -hex 16)/g" .env
📋 (Optional) Add your custom CA
If your GitLab instance is using a TLS certificate signed with your own Certificate authority (CA):
TEST-AND-EDIT
- Add the CA certificate file in
podman ?
📄 Prepare podman for launch
Generate podman network:
podman network create intranet
Generate podman socket
systemctl --user start podman.socket
systemctl --user enable podman.socket
If you encounter this error Failed to connect to bus: No medium found use these commands with your user as sudoer:
sudo loginctl enable-linger <your_local_user>
sudo systemctl --user -M <your_local_user>@ start podman.socket
sudo systemctl --user -M <your_local_user>@ enable podman.socket
Generate podman config files:
set -a; source .env; set +a
export uid=$(id -u)
envsubst < podman.yml.example > podman.yml
envsubst < configmap.yml.example > configmap.yml
Allow port 80 and above in system for local user:
- Add this line to /etc/sysctl.conf file as sudo user or root:
net.ipv4.ip_unprivileged_port_start=80 - Restart sysctl
sudo systemctl restart systemd-sysctl
🚀 Launch the application
You have successfully installed R2Devops on your server 🎉
Now you can launch the application and ensure everything works as expected.
Run the following command to start the system:
podman play kube podman.yml --configmap configmap.yml --network intranet
If you need to reconfigure some files and relaunch the application, after your updates you can simply run the command again to do so.
podman play kube podman.yml --replace --configmap configmap.yml --network intranet
Did you encounter a problem during the installation process ? See the troubleshooting section.
⏫ Update
Follow these steps to update your self-managed instance to a new version:
- Navigate to the location of your
self-managedgit repository - Update it
git pull - Open the
.env.examplefile and copy the values ofFRONTEND_IMAGE_TAGandBACKEND_IMAGE_TAGvariables - Edit the
.envfile by updating values ofFRONTEND_IMAGE_TAGandBACKEND_IMAGE_TAGvariables with the values previously copied.envFRONTEND_IMAGE_TAG="<new frontend version>"
BACKEND_IMAGE_TAG="<new backend version>" - Restart your containers
set -a; source .env; set +a
export uid=$(id -u)
envsubst < podman.local.yml.example > podman.yml
envsubst < configmap.local.yml.example > configmap.yml - You have successfully updated R2Devops on your server 🎉
🔄 Backup and restore
Data required to fully backup and restore a R2Devops system are the following:
- Configuration file:
.env - Databases:
- PostgreSQL database of Jobs service
- Files data:
- File storing data about certificate for Traefik service
All these data can be easily backup and restored using 2 scripts from the installation git repository:
scripts/backup_podman.shscripts/restore_podman.sh
💽 Backup
To backup the system, go to your installation git repository and run the following command:
./scripts/backup_podman.sh 13
The script will create a backups directory and create a backup archive inside
it prefixed with the date (backup_r2-$DATE)
You can use a cron job to perform regular backups. Here is a cron job that launch a backup every day at 2am:
0 2 * * * /r2devops/scripts/backup_podman.sh 13
It can be added to your crontab with the command crontab -e. Check more
information about cron jobs
here.
🛳️ Restore
To restore a backup from scratch on a new system, follow this process:
- Be sure that your new system is compliant with requirements
- Copy the backup file on your new server
- Clone the installation repository
git clone https://gitlab.com/r2devops/self-managed.git r2devops
cd r2devops - If the IP address of your server changed from your previous installation, update your DNS records. See section 2 of domain configuration
- Launch the restore script
./scripts/restore_podman.sh 13 <path_to_your_backup_file>
Did you encounter a problem during the restore process ? See the troubleshooting section.